📦 Deploy an Existing App Container Image
If you already have an app you've built and you just need a place to easily deploy it, Quome's App Platform has you covered. Deploying your app in Quome has many benefits, including managed infrastructure, out-of-the-box security, and easier compliance.
🚀 Deployment Process Overview
We are constantly building and testing new features to improve the usability and security of the App Platform. Please feel free to reach out to support@quome.site with any feature requests and we will respond!
Example Deployment
We provide an example repository that demonstrates how to deploy an app to Quome. The repository contains a sample application along with Docker configuration, deployment scripts, and GitHub Actions workflows for CI/CD pipelines.
✅ What to Verify First
📦 Make sure your app is built as an OCI image
To deploy your container image in Quome, check that your app image is an OCI image, not any other format. Docker can quickly build OCI images for you (Docker images are OCI images under the hood). Refer to the Docker documentation for instructions on how to build your Docker container image.
🏪 Put your container in a private registry
Quome can pull your OCI image from a public or private container registry; Docker Hub or GitHub Container Registry (GHCR) are popular options. Refer to the Docker Hub or GHCR documentation for instructions to set up a private registry.
Unless your organization has different policies about your app's distribution, we recommend using a private registry to store proprietary container images. Refer to the Docker Hub or GHCR documentation to set up a private registry.
Create a Quome API Key
To programmatically deploy apps to the Quome platform, you will need an API key for Quome's REST API. Navigate to the "API Keys" section of the Quome SaaS app to generate and manage your API keys.
Be sure to include the Quome API key you generated in the authorization header of any request as a bearer token.
We are working to build a CLI for Quome that will simplify your experience with the platform. In the meantime, you can use the endpoints in our API documentation and authenticate using your Quome API key.
🔐 Create Secrets in Quome
Secrets are a Kubernetes construct that securely store small sensitive data like login credentials and API keys that your app uses. Quome simplifies creating, sharing, and managing Secrets to reduce the risk of misconfiguration.
Secrets can be created and managed from within the Quome SaaS app UI or through the Quome API.
Creating a secret in the Quome SaaS app
Navigate to the "Secrets" section of the Quome SaaS app, from there you can create new secrets and manage existing secrets. Currently we support creating generic secrets and docker credentials.
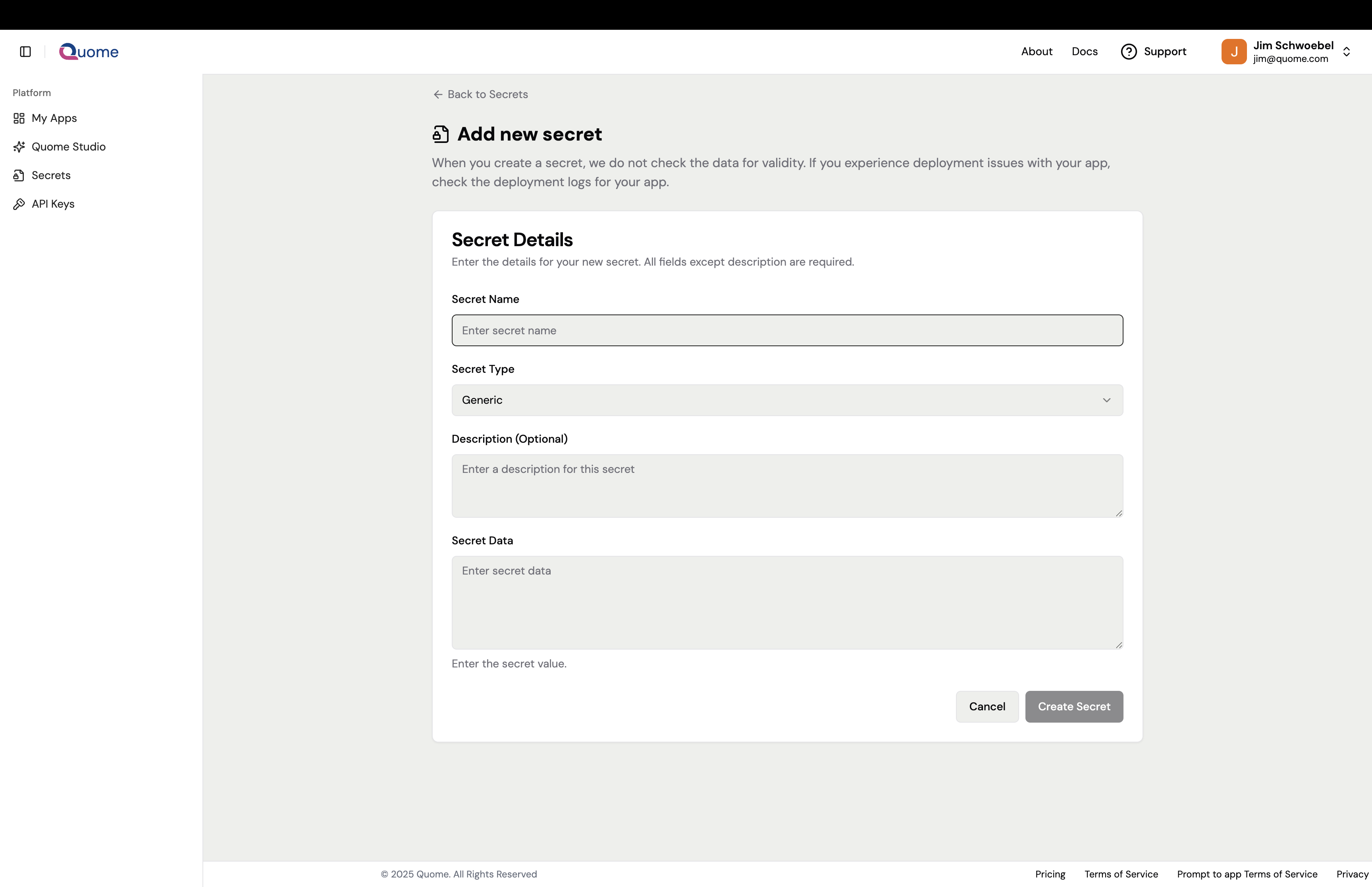 Create new secrets using the Quome SaaS app interface
Create new secrets using the Quome SaaS app interface
Generic secrets have the following body and support any generic string for the secret value.
{
"name": "my-secret-name",
"type": "generic",
"description": "A description for this secret",
"secret": {
"value": "YOUR_SECRET_VALUE"
}
}
Docker credentials secrets are in the same format as in docker config.json files. For example the following would be an example secret payload for dockerhub authentication using a username and personal access token.
{
"name": "docker-secret-name",
"type": "docker-credentials",
"description": "Docker Hub credentials",
"secret": {
"auths": {
"https://index.docker.io/v1/": {
"username": "YOUR_DOCKER_USERNAME",
"password": "YOUR_DOCKER_PAT"
}
}
}
}
Secrets are injected into the app as environment variables, defined in the app spec under a secret_vars block.
{
"secret_vars": {
"MY_SECRET_KEY_ENV_VARIABLE_NAME": "secret-key-name-in-quome-cloud",
"MY_SECRET_KEY_2_ENV_VARIABLE_NAME": "secret-key-2-name-in-quome-cloud"
}
}
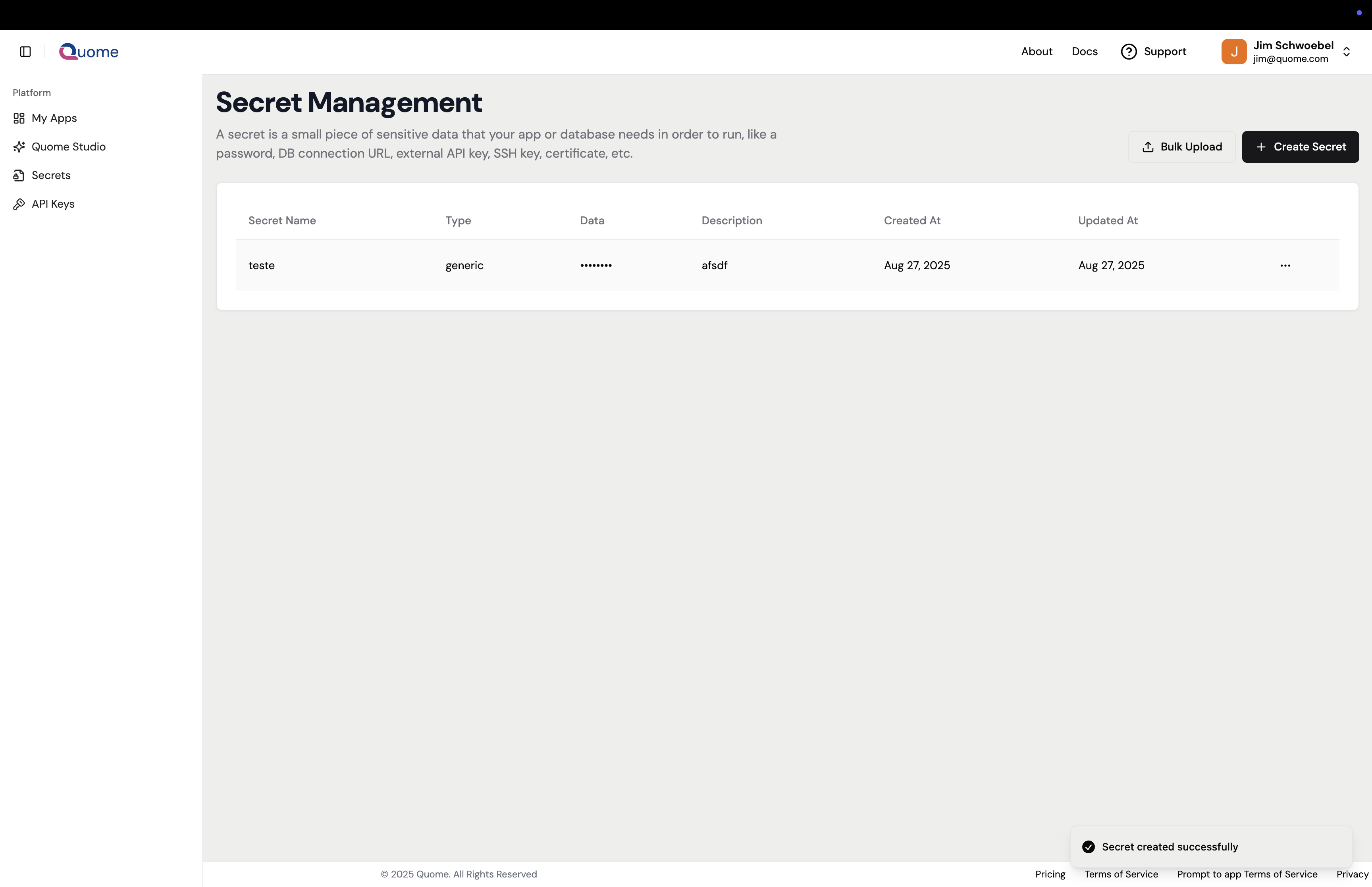 Manage and view all your organization's secrets in one place
Manage and view all your organization's secrets in one place
Create a docker-credentials Secret
First, Quome needs to securely connect to your private container registry in Docker Hub or GHCR in order to fetch your OCI image. To connect, you will need to create a Secret in Quome with the docker-credentials type.
To create this Secret programmatically, use the Quome API to send a POST request to the endpoint /orgs/:orgID/secrets, filling in the orgID with your Organization ID. The required parameters can be found in our API documentation.
Create Secrets for All Other Sensitive Fields
If your app has API keys, tokens, or any other credentials, store them in Secrets on the Quome platform before deploying your app. During deployment, you can choose the Secrets you want your app to use and Quome will automatically inject them into your app container as environment variables once deployed.
Use the Quome API to send a POST request to the endpoint /orgs/:orgID/secrets, filling in the orgID with your Organization ID. The required parameters can be found in our API documentation.
In your app code, be sure to refer to any sensitive data as an environment variable instead of hardcoding the data. The name of the environment variable should match the name of the Secret you create in Quome.
📋 Creating and Deploying your app spec
Apps are defined as a JSON object specifying the configuration for a number of docker containers to run on Quome.
At a minimum, if you just need to create an empty app to get an app ID (i.e. for a script) you can send a POST request to /orgs/:orgID/apps with the following body.
{
"name": "APP_NAME"
}
A complete app spec contains a few more blocks, depending on whether you want to include a persistent volume for a sqlite databaes, inject secrets, or configure envionrment variables.
- Environment variables are defined under the
env_varsblock, and are injected as is, - The
registry_secretparameter should contain the name of thedocker-credentialssecret you've already created. tmp_dirscan be added if any temporary directories are required
{
"name": "APP_NAME",
"spec": {
"port": "PORT",
"containers": [
{
"image": "DOCKER_IMAGE",
"name": "APP_NAME",
"port": "PORT",
"tmp_dirs": ["/tmp"],
"env_vars": {
"AN_ENV_VAR": "env-var-value"
},
"secret_vars": {
"SECRET_ENV_VAR": "secret-name-in-quome-cloud"
},
"sqlite": {
"mount_path": "/var/lib/",
"size": "1Gi"
},
"registry_secret": "docker-secret-name-in-quome-cloud"
}
]
}
}
🗄️ Deploying Your Database
If you are using SQLite as your app's primary database system, you just need to include the sqlite block in your app's spec, and Quome will automatically attach a persistent volume to your app and inject the path to that volume as an environment variable during deployment.
The following is an example sqlite block.
"env_var": "ENV_VAR_NAME"is optional but will rename the default env var fromSQLITE_DB_PATHtoENV_VAR_NAME- Mount path can be customized but must be within
/var/lib/i.e./var/lib/foo/would be allowed but/opt/bar/would not
{
"sqlite": {
"mount_path": "/var/lib/",
"env_var": "ENV_VAR_NAME",
"size": "1024Mi"
}
}
At this time, Quome does not take any backups or snapshots of your database, although this is in our roadmap. Please be careful to manually take backups of your data--a simple way to do this is to just copy the SQLite file to an object store like S3.
Non-SQLite Databases
While Quome currently doesn't offer managed Postgres, MySQL, or other types of database systems, we are working hard to bring these capabilities to you as part of our product roadmap.
However, you can connect an external Postgres, MySQL, or other database to your app today. Simply create a Secret in Quome that contains your database connection string and Quome will inject this into your app container. The name you give your Secret will be the name of the environment variable that is injected. Your app code should simply reference this environment variable to open and close database connections.
Since Quome isn't managing your external database, please keep in mind that we can't monitor or control anything including your database logs. Any incidents in your external database are your responsibility.
Custom container arguments
Quome supports specifying custom arguments in the app spec, which will be passed into the startup command for the docker container being served, this can be useful in cases where you are using a pre-built docker container, or the same image for multiple different purposes.
Simply add an args block to your app's spec under the particular container you want to pass args into.
{
"containers": [
{
"image": "DOCKER_IMAGE",
"name": "APP_NAME",
"port": 8000,
"args": ["run-service", "--arg_1", "foo", "--arg_2", "bar"]
}
]
}
📦 Sidecar containers
Sidecars are additional containers running in the same pod as the main app container. You may want to deploy an app with certain services as sidecars such as caches, telemetry services, etc.
While it is possible to run apps with a number of sidecar containers, as they are all running in the same pod they are subject to the same total resource limits and quotas, you may run into resource limitations if you attempt to run too many computationally heavy containers in the same app, this is particularly easy to run into when deploying AI models as sidecars.
Deploying a sidecar container is as simple as defining an additional container in the app spec and pushing that to the Quome API. For example, the following is an app spec for an app using a valkey cache as a sidecar container.
{
"name": "APP_NAME",
"spec": {
"port": 8000,
"containers": [
{
"image": "DOCKER_IMAGE",
"name": "APP_NAME",
"port": 8000,
"env_vars": {
"VALKEY_URL": "redis://0.0.0.0:6379"
}
},
{
"image": "valkey:7-alpine",
"name": "valkey-cache",
"port": 6379,
"tmp_dirs": ["/data"],
"args": ["valkey-server", "--save", "60", "1", "--loglevel", "verbose"]
}
]
}
}